Veriato User Activity Monitoring Can Help Your Organization…

Get Accurate Evidence
Make sure your organization has the logs, audit trails and the ability to analyze the data being collected. Employee investigations software can help collect the necessary evidence to make an effective case.

Stay Compliant
Many organizations deal with complex corporate and regulatory compliance requirements and audits. Some violations require internal investigations. Employee investigation software makes staying compliant and running audits much easier, with real-time alerts to customizable reporting and dashboards.

Ensure Fair Process
An internal employee investigation can be a very sensitive matter, dealing not only with data breaches and theft but also discrimination, harassment and so on. It is crucial to keep the process impartial and fair to safeguard employee and company reputation. Employee investigation software can help keep the process organized and impartial.
Create a Digital Paper Trail to Ensure Efficient & Effective Workplace Investigations
Powerful Workplace Investigation Tools
Veriato helps companies create a digital paper trail to ensure transparent and fair workplace investigations and simpler, faster audits.
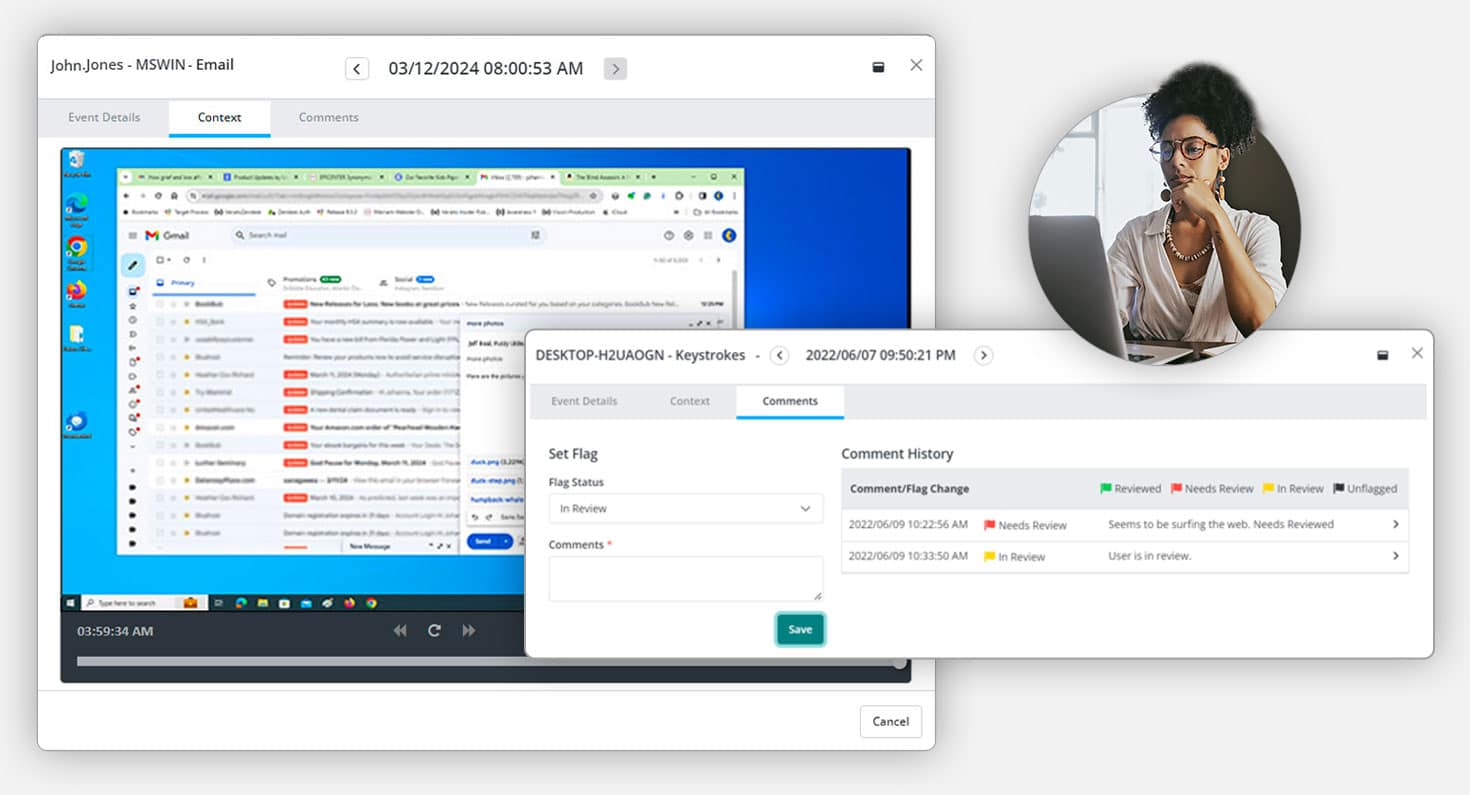
Email & Chat Monitoring
Capture communications activity in traditional email clients as well as many popular chat and messaging applications.
Web & Application Use
Categorize websites and applications as productive or unproductive.
Screenshots
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Keystroke Logging
Record every keystroke, including “hidden” characters and combinations and trigger real-time alerts based on specific keywords.
File & Document Tracking
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Network Activity
Autonomously capture connections made by applications, including ports used and bandwidth consumed.
Discreet Deployment
Veriato software can be deployed silently and remotely from a cloud-based admin console, if you don’t wish to alarm the target of your investigation.
Fully Customizable Settings
Set flexible work hours by team/department and decide when tracking starts and ends throughout the day.
Reports & Real-Time Alert
Choose from many preset reports or customize your own. Set up real-time alerts that fit your productivity metrics.
Hear From Actual Customers
Common Employee Monitoring Questions
What Are Workplace Investigations?
Workplace investigations are systematic inquiries conducted to resolve issues and allegations within an organization. These investigations are crucial for verifying facts, determining the validity of claims related to misconduct, and ensuring compliance with laws and company policies. They play a significant role in identifying and mitigating risks, safeguarding assets, and maintaining a healthy workplace culture.
What Are The Types of Workplace Investigations in Business?
Workplace investigations can vary widely, encompassing several types tailored to the specific needs of businesses, from small and medium-sized businesses (SMBs) to larger enterprises. These investigations can include compliance audits, security breaches, allegations of harassment or discrimination, and insider threat detections. Each type necessitates a different approach and tools, emphasizing the need for adaptable and scalable solutions in the IT landscape.
What is Employee Investigation Software?
Employee investigation software is a set of tools designed to streamline the process of conducting workplace investigations. It gives IT departments the ability to efficiently and discretely gather evidence, monitor activities, and ensure compliance with internal policies and legal regulations. This software plays a crucial role in preemptively identifying potential issues and resolving ongoing investigations with minimal disruption to business operations.
Why Deploy Employee Investigation Software?
- Get Accurate Evidence: Collects logs and audit trails essential for effective case building.
- Stay Compliant: Facilitates compliance with corporate and regulatory requirements through customizable reporting and real-time alerts.
- Ensure Fair Process: Maintains impartiality in sensitive investigations, protecting both employee and company reputations.
What Are The Key Features of Our Workplace Investigation Software Solution?
Our solutions offer powerful tools designed to detect and address financial fraud, data theft, and other forms of employee misconduct within organizations.
-
- Comprehensive Monitoring and Tracking: Our solution encompasses email and chat monitoring, web and application use analysis, along with detailed screenshots and keystroke logging to capture a wide range of employee activities.
- Discreet Operational Tools and Customization: The software allows for silent remote deployment and provides fully customizable settings to ensure discreet monitoring tailored to specific organizational needs.
- Insightful Reporting and Real-Time Alerts: It offers customizable reports and real-time alerts, enabling organizations to quickly identify and address potential issues, ensuring compliance and enhancing productivity.
Why Are Employee Investigations Important?
Employee investigations are essential for safeguarding the integrity and security of any organization. They help in promptly addressing allegations of misconduct, ensuring regulatory compliance, and maintaining a transparent and fair workplace. By identifying and mitigating risks, investigations contribute to the overall health and success of an organization.
How To Get Started with Veriato?
- Recognize Your Organization’s Needs: Understand the specific investigation requirements of your organization.
- Schedule a Demo: Arrange for a demonstration to see how Veriato can assist your organization in conducting more effective and efficient workplace investigations.
- Implement Veriato: Confidently deploy Veriato’s solutions to collect evidence, establish a digital paper trail and conduct thorough investigations.
Other Frequently Asked Questions
How does Veriato ensure the privacy and security of monitored data?
We prioritize data security and privacy by employing advanced encryption methods and strict access controls to protect monitored data, ensuring that sensitive information remains confidential and secure.
Can Veriato’s software be customized for different industry regulations?
Veriato is designed to be highly customizable, allowing it to meet a variety of business requirements. You have full control over what user activity data is being collected and how it is stored. There are hundreds of dashboards and reports to choose from and alert parameters are fully customizable.
How can employee investigation software improve workplace productivity?
By monitoring and analyzing employee activities and productivity levels, businesses can identify inefficiencies, provide targeted feedback, and implement strategies to enhance overall productivity and performance.
Additional Employee Investigations Resources

Smoother Workforce Investigations With Behavior Analytics
Workplace Investigations - Difficult, but Critical Workplace investigations are a critical function of IT, information security and HR teams across most organizations. From data breaches to fraud and company policy violations, investigations can be difficult and time...

How to Use Workplace Investigation Software
Human Resources departments are typically tasked with conducting workplace investigations into allegations of misconduct or criminal activity. Every complaint or allegation has the potential to turn into a lawsuit or criminal case, which is why it’s so important to...

Protect Your Business with Digital Forensics Software
The world has been moving toward a fully connected workplace model for years, even prior to COVID-19. Now, understanding your company’s digital presence - and footprint - is more important than ever. Everything you or your employees do online could have lasting...




