Boost Productivity and Security with Veriato UAM
Comprehensive User Activity Monitoring
Track an extensive array of activities, including email, chat, application use, web browsing and more.
Productivity
Insights
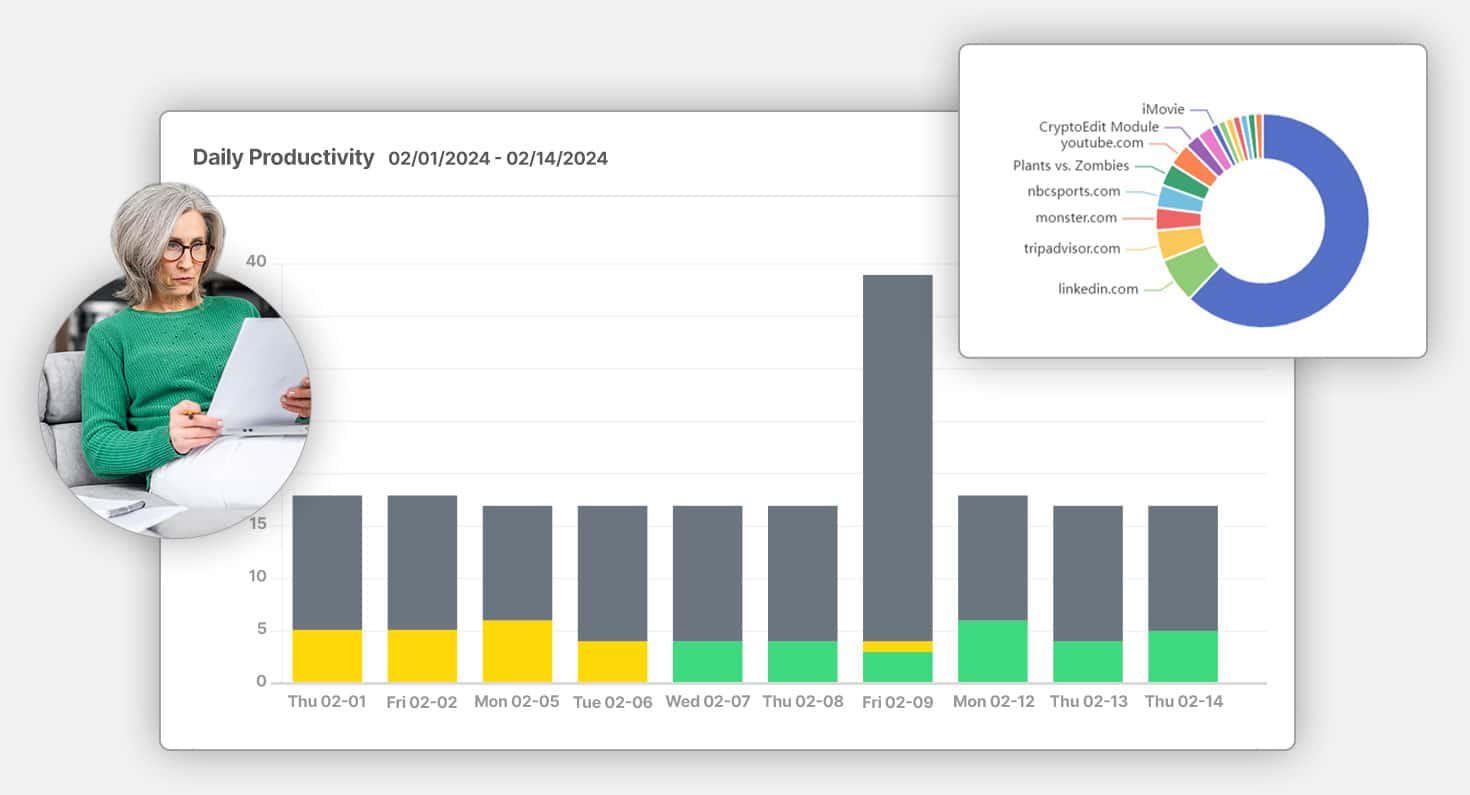
Identify unproductive behaviors and enhance workforce efficiency with detailed analytics.
Compliance
Oversight
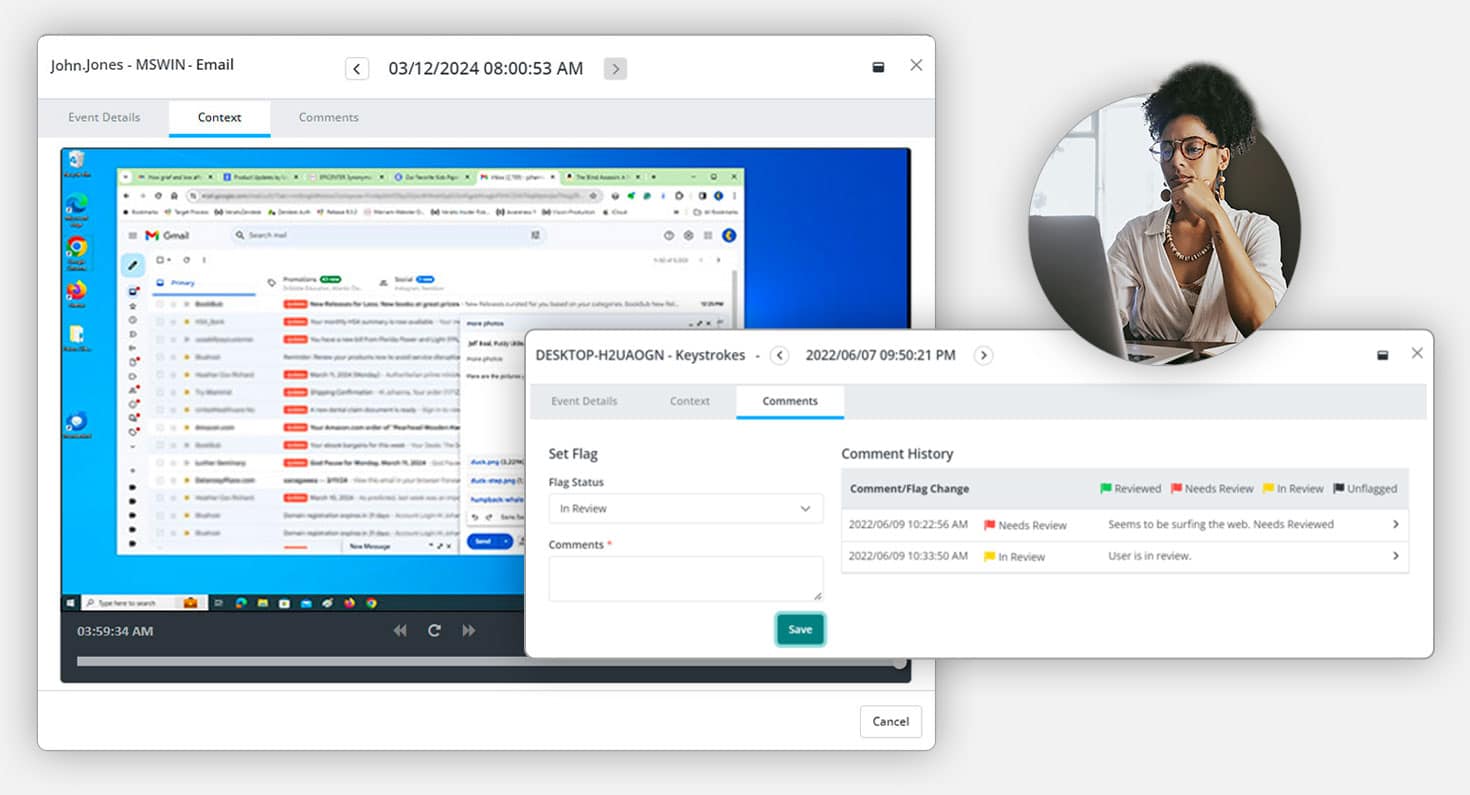
Gain complete visibility into user activities to detect signs of policy breach to ensure compliance.
Seamless
Integration
Deploy quickly with your existing infrastructure, whether on-premise, cloud, or hybrid.
Solve Today’s Workforce Challenges with Veriato UAM

Most Employees Are Disengaged
77%
of employees globally are disengaged*

“Quiet Quitting” Poses a Real Security Risk
59%
of global workforce can be categorized as quiet quitters*

The Cost of Doing Nothing is High
$8.8 Trillion
in lost productivity by disengaged workers*
* Gallup, State of the Global Workplace: 2023 Report
Gain Insight and Control Over Employee Activities
Spot Productivity Issues
Uncover Compliance Risks
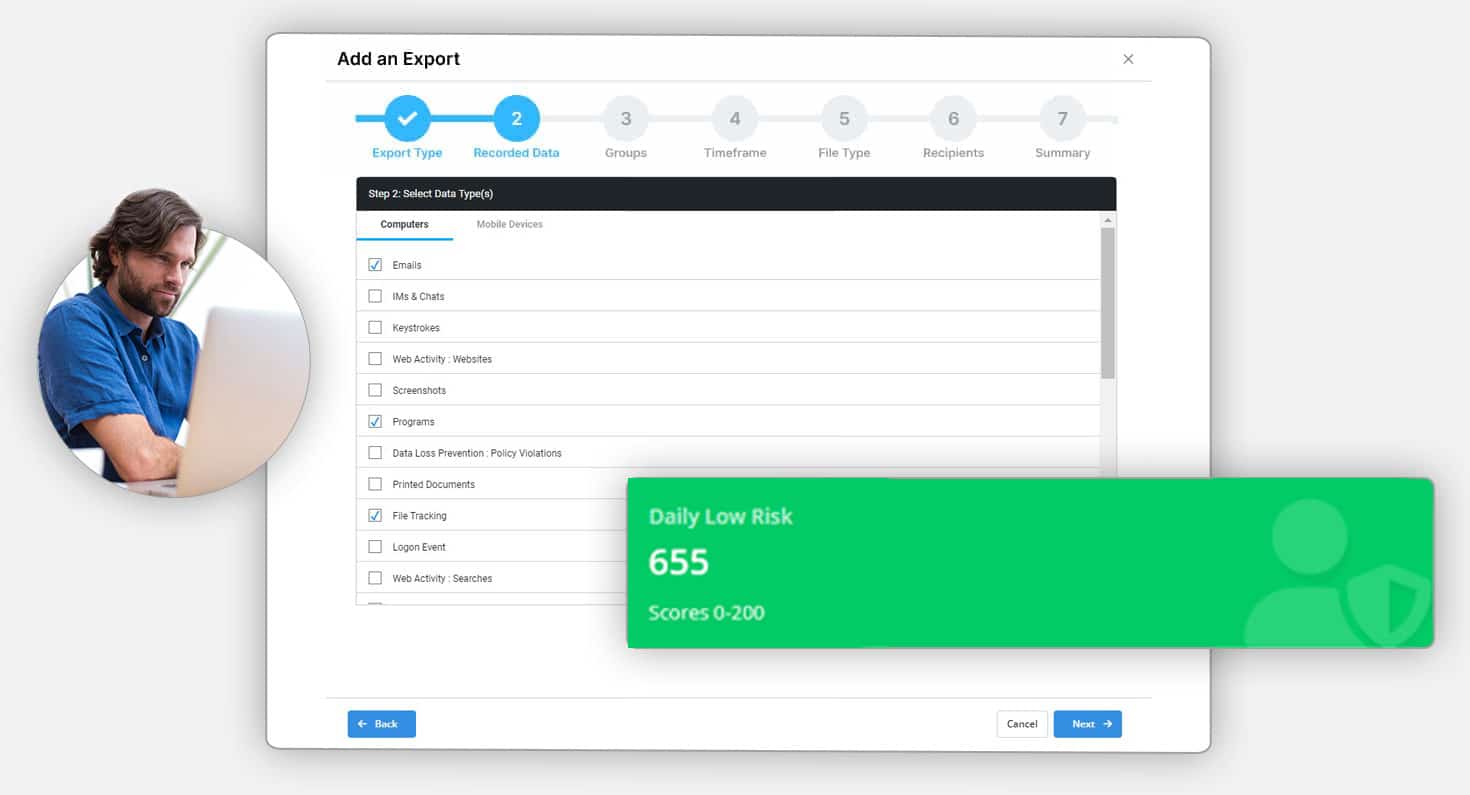
Improve Cybersecurity Posture
Creating a secure and productive work environment is essential in today’s evolving threat landscape. UAM enhances your cybersecurity posture by tracking a wide range of activities, setting up real-time alerts for suspicious activities, and utilizing advanced analytics to understand and predict employee behavior. Integration with other security solutions, such as Data Loss Prevention (DLP) and Security Information and Event Management (SIEM), provides a unified security approach.
Identify Risky Activity
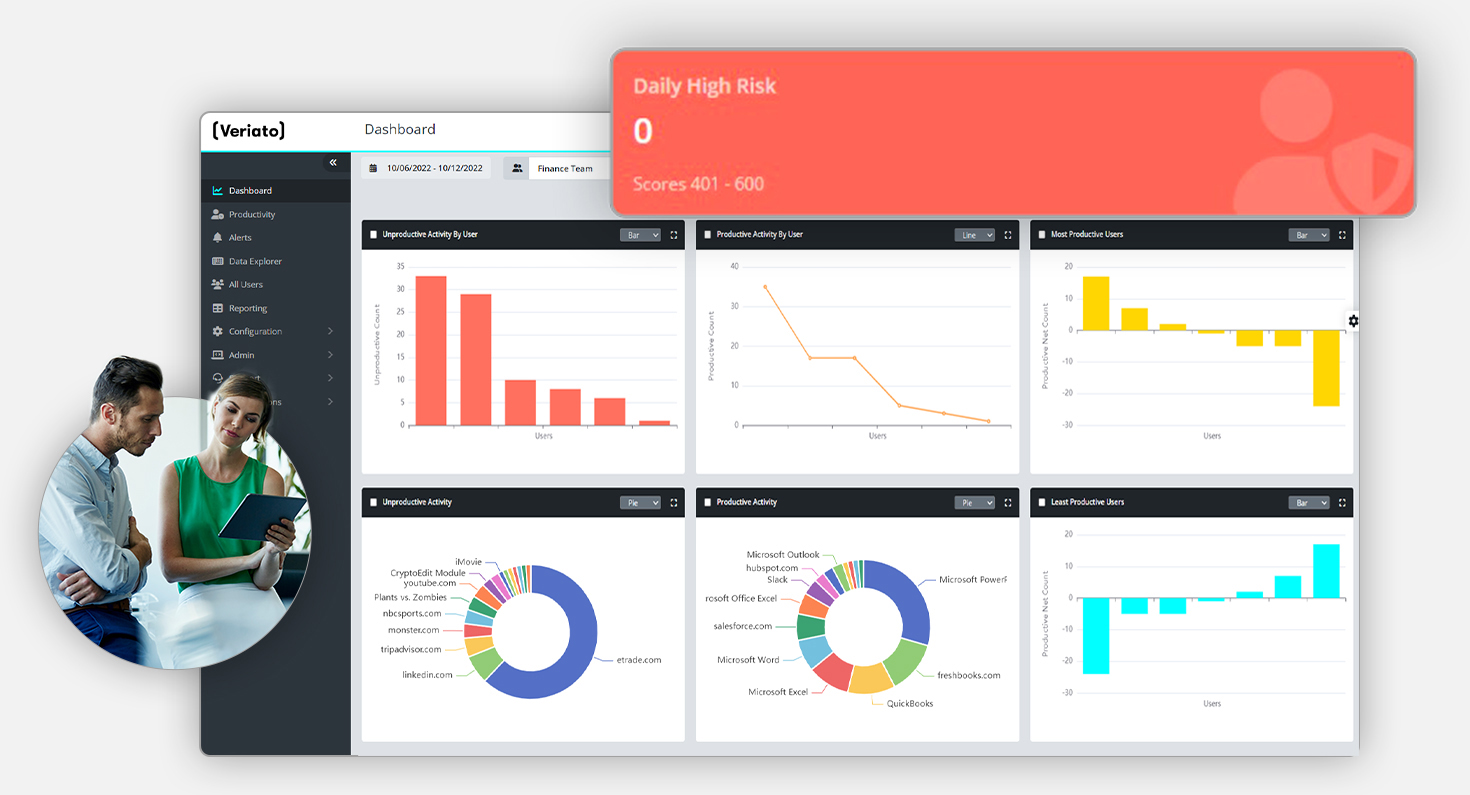
Key Features of User Activity Monitoring (UAM)
Email & Chat Monitoring
Monitor communications in traditional email clients and popular chat and messaging applications for comprehensive oversight.
Web & Application Use
Categorize websites and applications as productive or unproductive to optimize employee performance.
Idle and Active Time Tracking
Track the minutes an employee’s computer is idle or active during the workday to gain productivity insights.
File & Document Tracking
Monitor activities on local, removable, and cloud storage, as well as print operations. Track when files are created, edited, deleted, or renamed.
Network Activity
Automatically capture connections made by applications, including ports used and bandwidth consumed.
Fully Customizable Settings
Set flexible work hours by team or department and control when tracking starts and ends each day.
Screenshots
Select from continuous, keyword-triggered, or activity-triggered screenshots for detailed activity analysis.
Reports & Real-Time Alert
Utilize a variety of pre-set reports or create custom ones tailored to specific needs. Set up real-time alerts aligned with your productivity metrics to stay informed of critical activities.
Seamless Implementation and Flexible Deployment
On Premise
Deploy on your own servers for maximum control and customization.
Cloud
Leverage our secure cloud services or rapid, scalable deployment.
Our solutions ensure minimal disruption during integration, allowing you to quickly enhance security and productivity. Book a demo today to learn more about our easy deployment options.
What Clients Have to Say
Common User Activity Monitoring Software Questions
What Is Employee Monitoring Software?
Employee monitoring software is used to track employee activities, attendance and productivity. This includes any kind of digital activity performed on company-owned or registered devices.
By providing insights into employee work habits and behavior, this technology helps employers streamline operations, safeguard sensitive information, and maintain compliance with regulatory standards.
Can employee monitoring software improve productivity?
Yes, by providing insights into work habits and identifying inefficiencies, it can help managers make informed decisions to boost productivity, manage resources better, and support employees needing guidance or training.
What features and benefits should I look for in employee monitoring software?
Key features and benefits of user activity monitoring software include time tracking, productivity analysis, application, and web usage monitoring, file and document tracking, real-time alerts, customizable user analytics reports, and compliance tools. Advanced solutions may offer AI-driven behavioral analysis, anomaly detection, and protection against insider threats.
Does employee monitoring software invade privacy?
While it can raise privacy concerns, proper implementation respecting legal guidelines and focusing on professional activities minimizes intrusion. Clear communication about monitoring policies and securing collected data are critical practices.
How can companies ensure they use employee activity monitoring software ethically?
Businesses should use the software transparently, focusing on performance and security objectives rather than intrusive surveillance. They should also respect employee privacy by monitoring work-related activities and securing the data collected.
Can employee activity monitoring software be used for remote workers?
Absolutely. It’s particularly useful for managing remote teams by tracking productivity and ensuring security across distributed work environments, offering managers visibility into remote work patterns.
How do employees typically react to monitoring software?
Reactions can vary based on the implementation and communication strategy. Transparency, clear guidelines, and using the software for constructive feedback and support can lead to more positive acceptance.
Can user monitoring software help with compliance and legal requirements?
Yes, it can assist in maintaining compliance with various regulations by monitoring and reporting on work activities, helping prevent insider threats such as unauthorized data access, and ensuring that work hours and activities are in line with legal standards.
What Makes Our Employee Activity Monitoring Software Special?
Enhanced Productivity
Our user activity monitoring software allows companies to track employee activities, enabling them to identify workflow bottlenecks and inefficiencies. By optimizing work processes, companies can boost productivity, resulting in increased output and profitability.
Data-Driven Decision-Making
The software provides valuable insights into user behavior and work patterns. This data can be used to make informed decisions about resource allocation, project planning, and strategic initiatives, leading to better business outcomes.
Compliance And Security
We help companies adhere to regulatory requirements and security protocols. It ensures that sensitive information is protected and that employees follow compliance guidelines, reducing the risk of data breaches and legal issues.
Employee Accountability
By monitoring employee activities, the software fosters a sense of accountability among staff members. Knowing their actions are tracked encourages employees to stay focused and committed to their tasks, resulting in improved job performance.
Remote Work Management
With the rise of remote work, our software aids in managing remote teams effectively. It allows organizations to monitor remote employees’ activities, ensuring they remain productive and aligned with company goals even when working from different locations.
Legal Protection
The software can serve as a valuable source of evidence in disputes or legal challenges. It can provide a comprehensive record of employee activities, helping organizations protect themselves in legal matters and investigations.
Employee Satisfaction
When employees understand that monitoring is implemented for security and performance improvement rather than micromanagement, it can lead to a sense of security and job satisfaction, as they can trust that their company is taking measures to create a safe and productive work environment.
How does user activity monitoring software work?
Remote monitoring software is available for PCs, Macs, Chromebooks and Android devices. Once installed, it can run discreetly in the background.
This software will track and record detailed information about all the user’s activity. In fact, you can even access a history of the user’s web searches, idle time, instant messages, file movement, productivity, downloads, uploads, print jobs, USB device usage, network access, and more.
Every time a new program is opened, the software will automatically time how long it is used. This information is compiled into a productivity tracking report so you can see how your employees are spending most of their time.
Remote monitoring software also acts as a digital surveillance camera by recording the user’s screen, utilizing user analytics to provide a comprehensive view of activities and productivity patterns. This allows you to ascertain their activities and understand their productivity and time-consuming tasks.
At Veriato we simplify employee productivity monitoring by using powerful tools to keep your remote, hybrid and office teams productive.
What Are The Benefits of Workforce Productivity Monitoring?
User monitoring software gives companies visibility and peace of mind.
- Spot productivity issues before they become problematic
- Support remote workforce by uncovering potential gaps or inefficiencies
- Increase trust in remote employees with regular reports for managers
- Give managers more insights to have informed conversations with employees
- Ensure that your employees and contractors are not violating company policies or federal regulations
Employee monitoring has other benefits outside of productivity, including:
- Regulatory compliance & auditing
- Malicious or illegal activity detection
- Insider threat detection
- Evidence for employee investigations
- Data breach response improvement
- Who Uses Employee Monitoring Software?
Who should consider implementing User Activity Monitoring (UAM) in their organization?
User Activity Monitoring (UAM) is beneficial for a wide range of organizations and industries, particularly those that prioritize security, compliance, and productivity. Here are some key groups that should consider using UAM:
Security-Conscious Organizations:
- Financial Services: Banks, investment firms, and insurance companies handling sensitive financial data can use UAM to detect and prevent insider threats.
- Healthcare: Hospitals, clinics, and healthcare providers must protect patient information and comply with regulations such as HIPAA.
- Legal Firms: Law firms managing confidential client information can benefit from monitoring to ensure data security.
Compliance-Driven Industries:
- Regulated Sectors: Businesses in highly regulated industries (e.g., pharmaceuticals, energy, and government) can use UAM to ensure compliance with industry standards and regulations.
- Educational Institutions: Schools and universities can monitor network usage to comply with safety regulations and prevent misuse of IT resources.
Remote and Hybrid Work Environments:
- Remote Teams: Companies with remote or hybrid workforces can use UAM to maintain visibility into employee activities and ensure productivity.
- IT Departments: IT professionals can monitor network activity, troubleshoot issues, and ensure secure access to company resources.
Organizations Handling Sensitive Information:
- Research and Development: Companies in R&D sectors can protect intellectual property and sensitive project data through comprehensive monitoring.
- Manufacturing: Manufacturers can monitor employee activities to safeguard trade secrets and maintain operational security.
Management and HR Teams:
- Human Resources: HR departments can use UAM to identify productivity issues, ensure fair usage of company resources, and investigate workplace incidents.
- Management: Managers can gain insights into employee performance, identify training needs, and support productivity improvement initiatives
User Activity Monitoring Software Resources

Beyond Productivity – Using UAM to Understand Team Capacity & Burnout Risk
Key Takeaways: Burnout and disengagement are leading causes of productivity loss and attrition. User Activity Monitoring (UAM) offers insights into workload balance, time-on-task, and behavioral patterns. HR and People Ops can use UAM to support wellness, engagement,...

Beyond the Perimeter: Rethinking Security from the Inside Out
Key Takeaways Insider Threats Are a Boardroom Issue, Not Just an IT Problem With rising accountability for compliance and resilience, CISOs must own internal risk visibility as part of their strategic mandate. Traditional Tools Can’t Tell You Why Risk Is...

Redefining Accountability: How User Activity Monitoring Supports Remote Workforce Management
Key Takeaways Stop guessing and start guiding. UAM provides the visibility to act early and lead with confidence. Accountability that motivates. Use real insights to empower employees, not punish them. See the friction that’s slowing you down. Identify hidden...




