Thousands of Customers Across Hundreds of Thousands of Endpoints Globally





Next-Generation Predictive Behavior Analytics & Risk Intelligence
Veriato offers predictive behavior intelligence built with AI to help organizations manage insider risk and monitor employee activity in their remote, hybrid and in-office environments.
Harness the Power of Generative AI
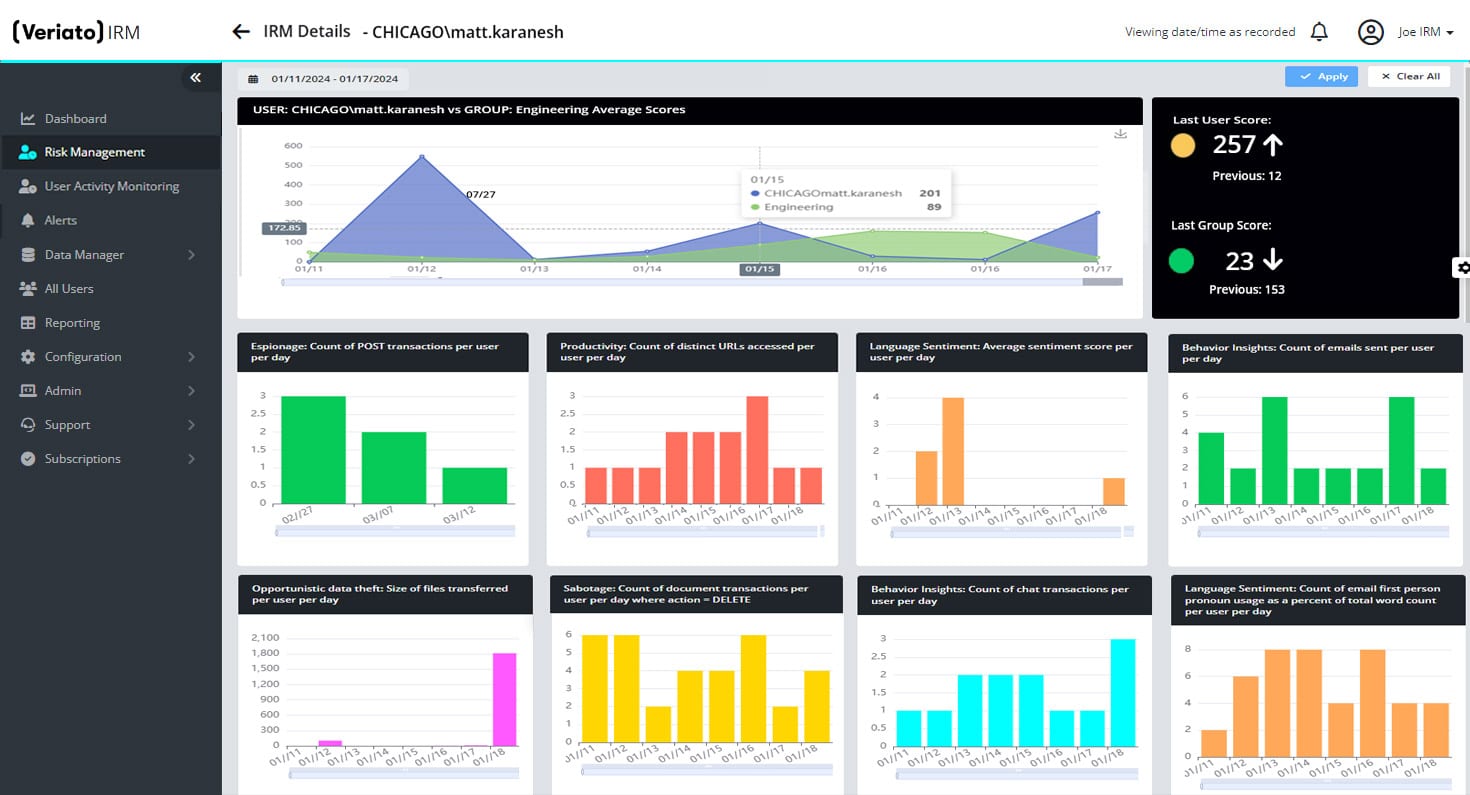
Unparalleled Risk Detection
Domain specific Generative AI trained with Retrieval Augmented Generation (RAG) for language analysis.
Complex Dimensional Analysis
Get a rich, multi-dimensional picture of user behavior with GenAI-driven Risk Scoring.
Powerful Anomaly Detection
Easily detect anomalous activity based on a rolling baseline unique to your organization.
Advanced Pattern Identification
Understand and analyze patterns across logon events, document activity, email activity and much more.
Comprehensive Language & Sentiment Analysis
Detect changes in tone and sentiment with Natural Language Processing (NLP) capabilities.
Automatic PII/PHI Identification
Use RAG pre-trained models to automatically identify sensitive information on screen for alerts or reduction.
Employee Productivity Analytics For Your Workforce
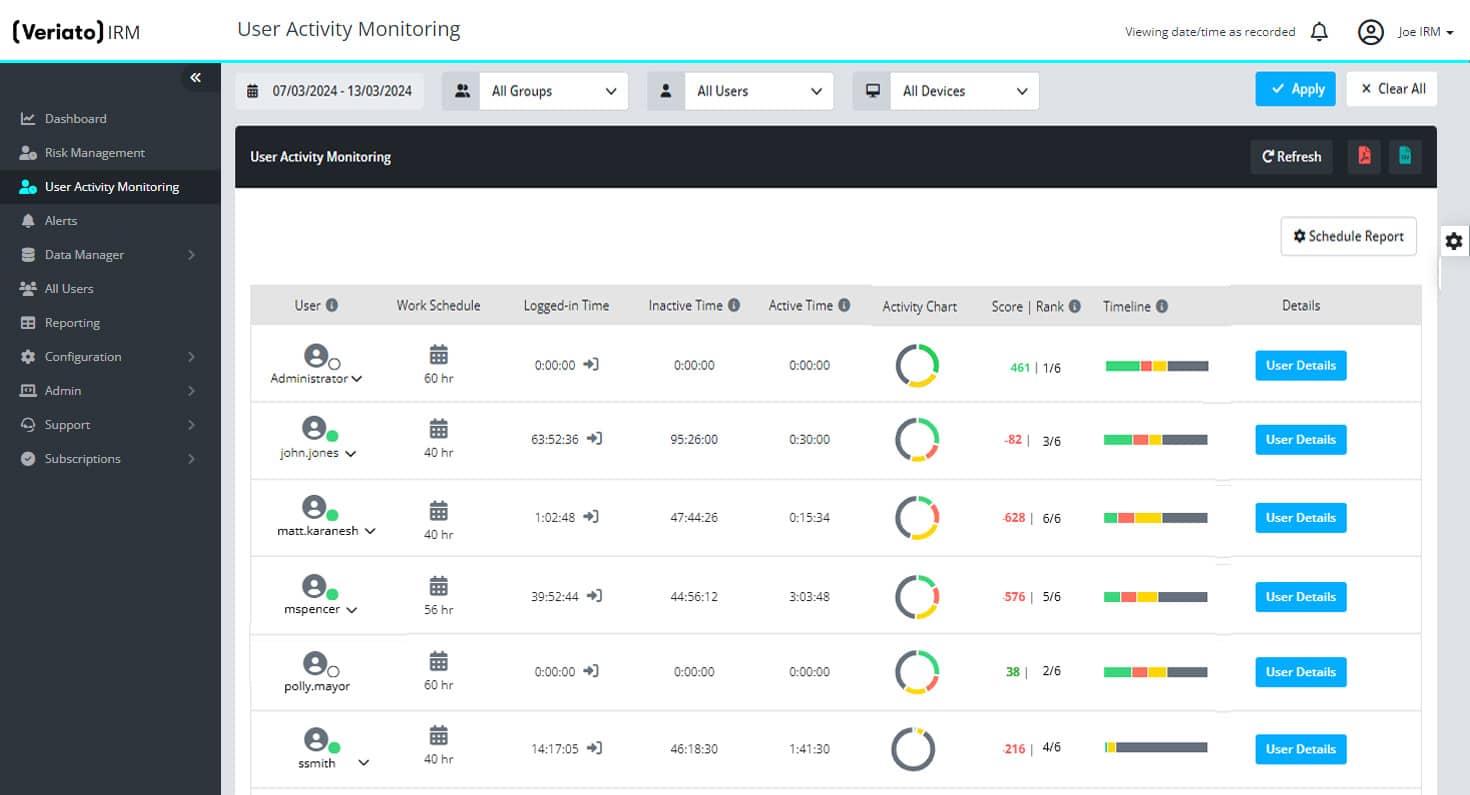
Idle and Active Time Tracking
Understand device idle and active time and generate productivity scores for each team member.
Web & Application Use
Assign productivity scores to websites, programs, and applications.
Screenshots
Select between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
File & Document Tracking
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Fully Customizable Settings
Set flexible work hours by team/department and decide when tracking starts and ends throughout the day.
Reports & Real-Time Alerts
Choose from many preset reports or customize your own. Set up real-time alerts that fit your productivity metrics.
Powerful Workplace Investigation Tools
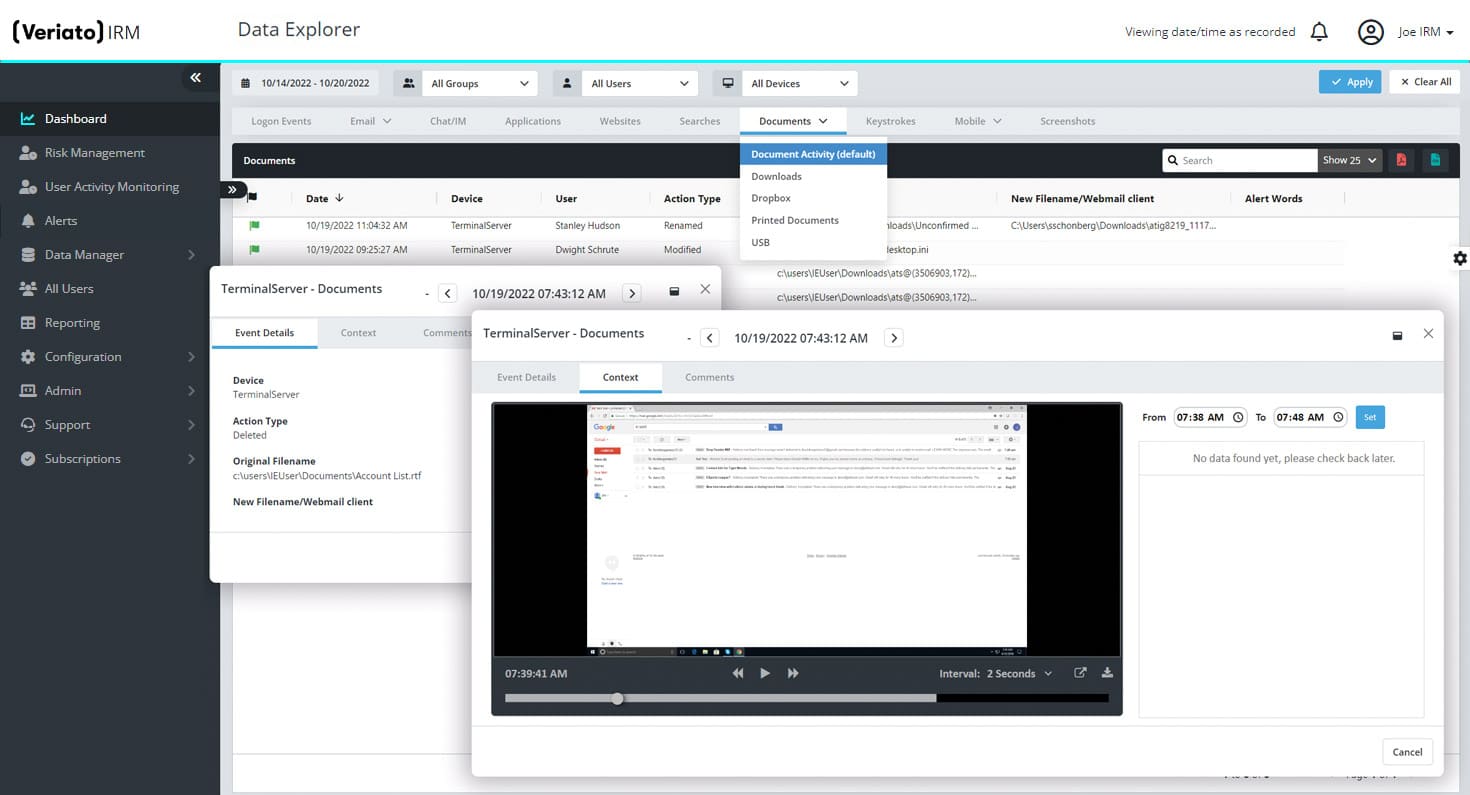
Web, Chat & IM Activity
Capture and report on communications activity occurring on commonly used messaging apps. Record web activity, including webmail usage, file uploads.
Email Monitoring
Capture and analyze communication activity in traditional email clients as well as many popular webmail services.
Screenshots
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Application Tracking
Collect all application usage to provide true reporting on what applications are being used, by who, and for how long.
Keystroke Logging
Record every keystroke, including “hidden” characters and combinations and trigger real-time alerts based on specific keywords.
File & Document Tracking
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Smarter Auditing & Compliance
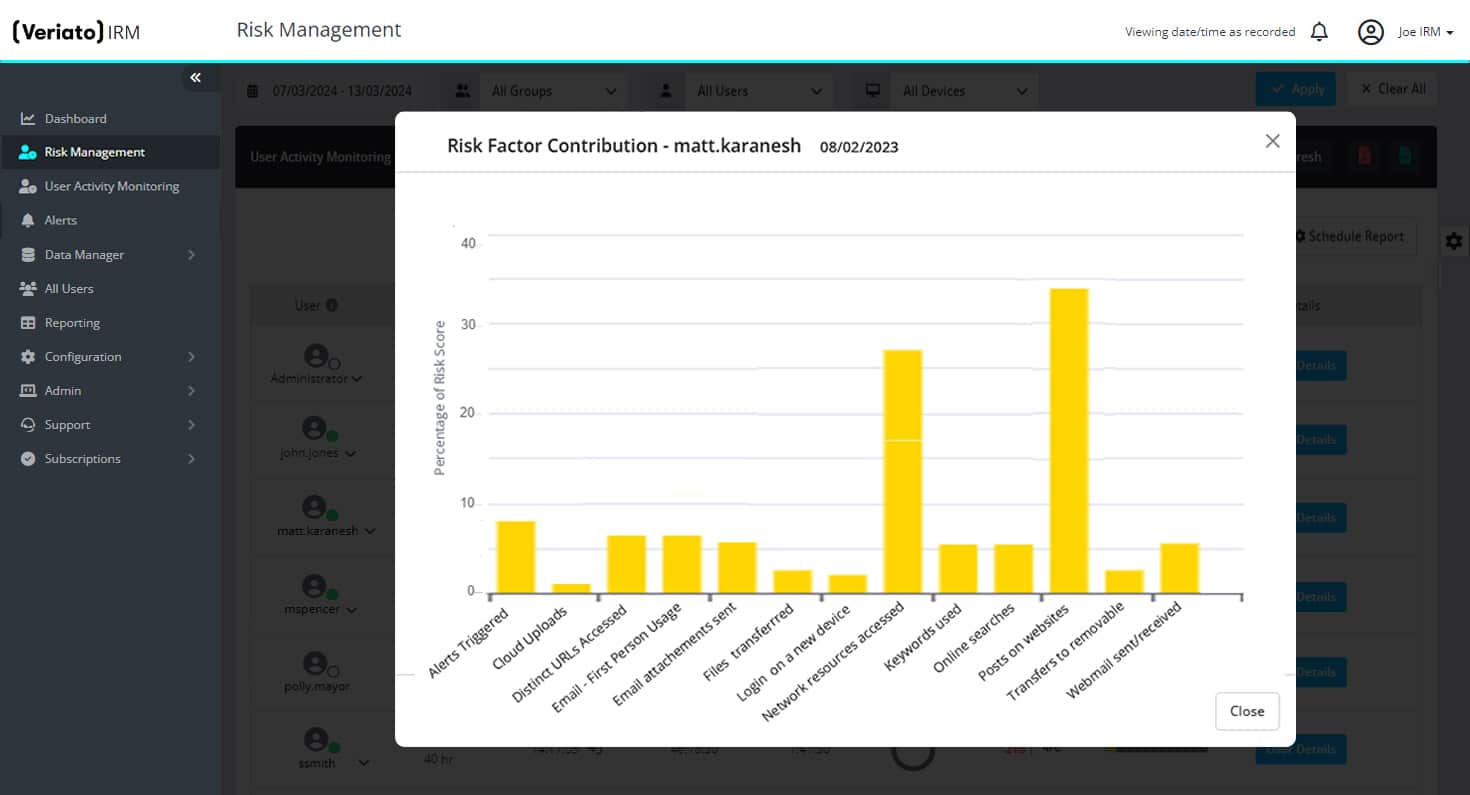
User Activity Monitoring
Ensure compliance by monitoring activity across applications, email, chats, files, internal network, web and much more.
Language Sentiment Analysis
Understand nuanced sentiment, spot potential employee issues and manage compliance with confidence.
Reports & Real-Time Alerts
Get reporting and real-time alerts whenever potential fraudulent or illegal activity is detected.
Screenshots
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Network Activity
Autonomously capture connections made by applications, including ports used and bandwidth consumed.
File & Document Tracking
Track activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
What Clients Have to Say
Veriato Works Wherever Your Team Works
| Android | Android 4 – 13 |
| Windows PC | Windows 7 – 11 |
| Mac | MacOS 10.8 – 12 |
| Chromebook | *All Chromebooks |
*HP, Asus, Dell, Lenovo, Acer, Samsung & Google


