Thousands of Customers Across Hundreds of Thousands of Endpoints Globally





Next-Generation Insider Risk & User Activity Monitoring Capabilities
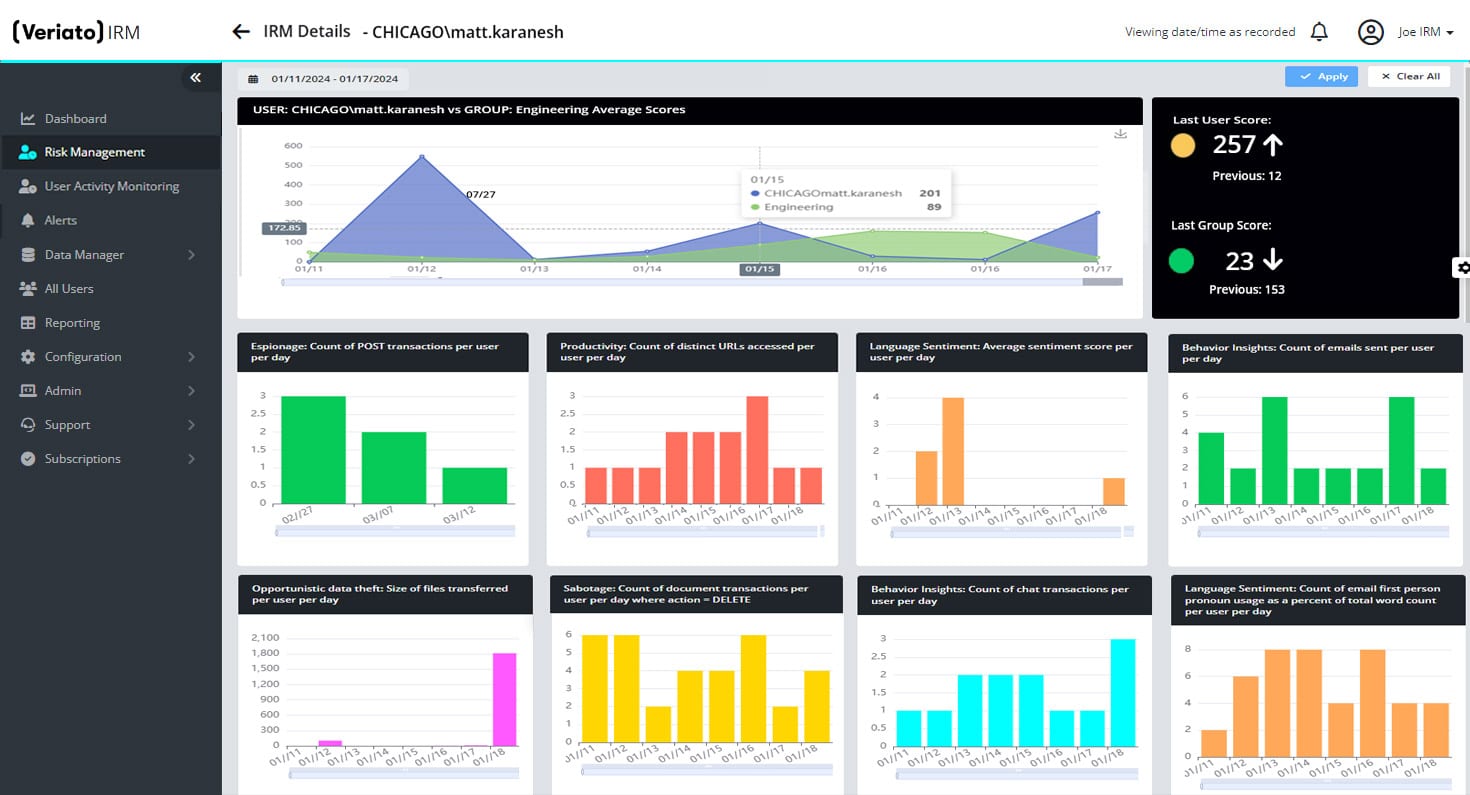
Insider Risk Management (IRM)
Get unprecedented insight into user behavior with GenAI-driven risk scoring, sentiment analysis and pattern identification.
- Unparalleled risk detection capabilities.
- Advanced behavior pattern identification across logon events, document activity, email activity and other user behavior.
- Comprehensive language and sentiment analysis.
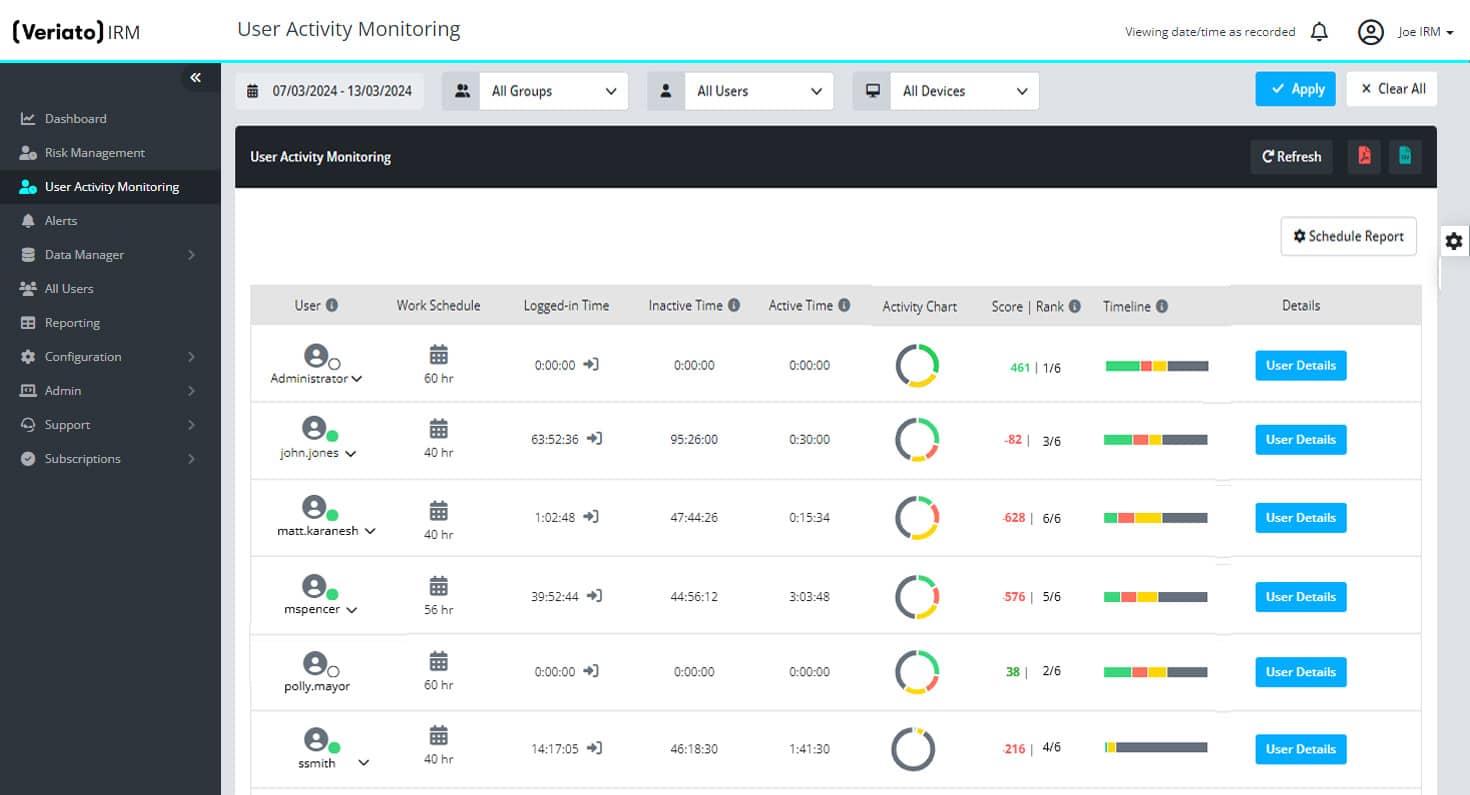
User Activity Monitoring (UAM)
Gain complete visibility into your employees’ activities to track productivity and spot compliance issues.
- Identify malicious or unsecure employee activity.
- Spot productivity issues.
- Detect fraud & potentially damaging behavior.
- Uncover compliance risk.
Let’s Get Started
Insider Risk & Employee Monitoring Resources

Is Employee Monitoring Software Worth The Investment?
Key Takeaways: Employee monitoring software offers detailed insights into employee activities, enhancing productivity and bolstering data security. Choose the right software based on features, cost, integration capabilities, and scalability to align with specific...

How To Choose The Right Employee Monitoring Software
Remote work is becoming increasingly common, and data breaches are a constant threat. The importance of employee monitoring software has never been more pronounced. For businesses looking to safeguard their digital assets while optimizing workforce productivity,...

UEBA: Revolutionizing Security With Advanced Analytics
Key Takeaways: Behavior-Focused Security: UEBA revolutionizes cybersecurity by analyzing user behavior patterns, providing a dynamic approach to detecting anomalies and potential threats. Flexible and Adaptable: Scalable for any organization size, UEBA integrates with...


